Secure your tokens, passwords, and secret data fields by encrypting variables in Assertible.
Try out encrypted variables now with a free Assertible account
Encrypted variables provide a new way to store tokens, passwords, and all sensitive data required by your tests to improve your team's API testing security practices. We at Assertible have taken extra care to ensure that encrypted variables are not only trivial to use, but build on cryptographically sound methodology for safe storage; continuing our tradition of making Assertible the easiest platform to test and monitor your web services.
Encrypting a variable is simple: anywhere you can create a variable, click the Encrypt variable check-box. Once your variable is saved, you're done:
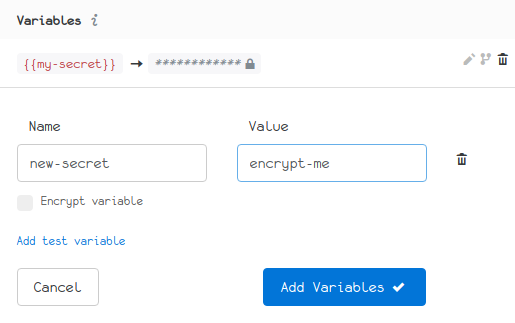
How it works
To understand how encrypted variables work, here is some basic information describing the security model we at Assertible have developed:
Encrypted variables are not stored on disk and never sent over the wire in an unencrypted format (e.g. plain text).
Encryption is done on the client-side, using an RSA public key that is specific to your individual web services.
Once a variable has been encrypted, it cannot be displayed or further edited.
Only the Assertible test runner has access to the private keys that are necessary to unencrypt encrypted variables.
To fully understand a security model, it's critical to identify the limitations. This allows us to gain an understanding of what it can and cannot guarantee. While we are dedicated to expanding and improving Assertible's security strengths, we would be remiss if we did not help your team identify the limitations of encrypted variables:
If an encrypted variable is interpolated anywhere in an HTTP request, it will be transmitted over the wire unencrypted.
This means that interpolated encrypted variables will end up in request logs; both in Assertible's dashboard and possibly your servers, depending on the extent to which your servers log request details.
Members of your team can retrieve the plain text of an encrypted variable by interpolating the variable in a field that may be logged by the test runner or on your server, such as a request body.
Encrypted variables provide their full potential when used in combination with an auth method that does not send any credentials over the wire. This is the case for Digest authentication and oAuth v1.0a.
If you use encrypted variables with other auth methods then your credentials end up in the test result request logs and will be stored on our side in the clear.
We are exploring options to lift this limitation and to allow the use of encrypted variables with all auth methods in a secure manner.
Our goal with this feature is to protect your data from malicious actors. However, it's critical to constantly audit your team's security processes using unbiased sources, like the Open Web Application Security Project (OWASP), to learn more about securing and protecting your application and its data.
For more information check out the documentation on encrypted variables.
You can check this feature out yourself using a free account. If you have a feature request or questions, feel free to send us a message or reach out on Twitter any time.
:: Christopher Reichert
Categories
The easiest way to test and
monitor your web services
Reduce bugs in web applications by using Assertible to create an automated QA pipeline that helps you catch failures & ship code faster.
Recent posts
Tips for importing and testing your API spec with Assertible 05/26/2020
New feature: Smarter notifications 5/17/2019
New feature: manipulate variables using jq 2/20/2019
Sync changes from OpenAPI/Swagger specifications with Assertible API tests 02/11/2019